Every month new vulnerabilities are found within Windows operating systems that potentially allow malware and/or ransomware into your environment. Malware and ransomware are notoriously difficult to remove and recover from. If you get infected then you will most likely be fully testing your backup solution to restore your environment. Everybody knows that you need to take measures to protect your environment by using antivirus and anti-malware software, but this can only fully protect you from already known treats. Is there anything else you can do to protect your environment?
One approach you can take is to lock your environment down such that only known software and scripts can execute. In Windows 7 Microsoft introduced the AppLocker feature which is an application white listing technology. It allows administrators to restrict the programs, windows installers, scripts and packaged apps users can execute based on the programs path, publisher or file hash. The feature is available in Windows 7, 8, 10 Enterprise Edition and Windows Server 2008R2 and above.
The purpose of this entry is to try and guide you in the way we suggest you implement AppLocker within your environment. How AppLocker works and detailed configuration of it is already very well documented by Microsoft here.
AppLocker is configured through group policy under the setting Computer Configuration->Policies->Windows Settings->Security Settings->Application Control Policies->AppLocker.
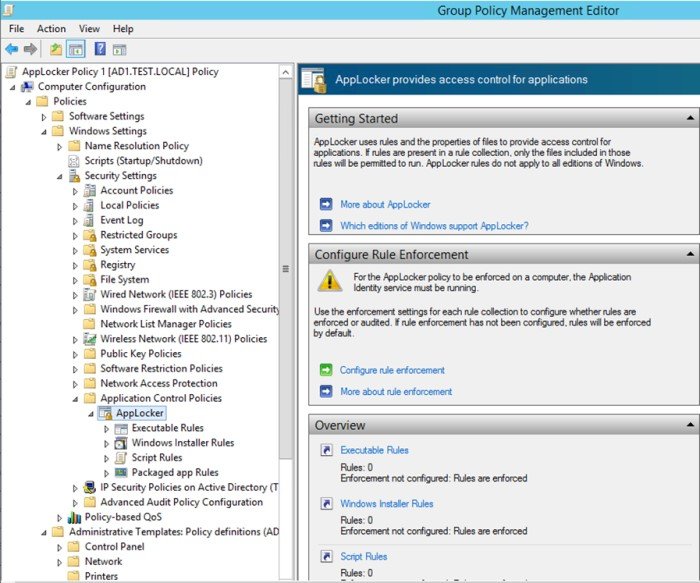
Implementing AppLocker within your environment needs some careful planning to ensure everything your users need to do their job can run. We recommend the below process when looking to implement AppLocker:
1. Create a group policy object at a suitable level AD container level so that it will apply to the server you are looking to enforce AppLocker on.
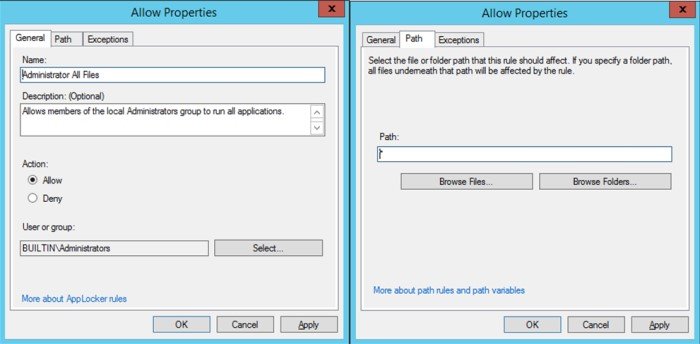
2. Add a Path rule to each collection you want to enforce to allow members of the BUILTIN\\Administrator to run everything (*). This allows administrators to perform any activity.
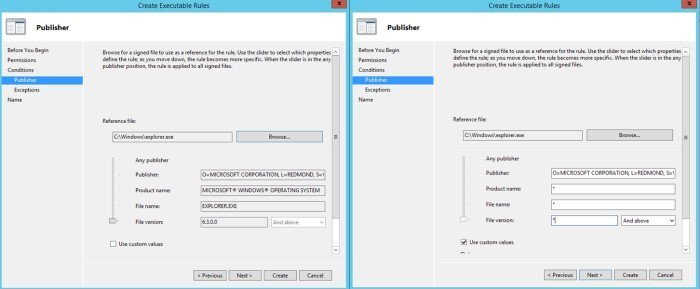
3. Add a publisher rule to each collection you want to enforce to allow Everyone to run items signed by ‘O=MICROSOFT CORPORATION, L=REDMOND, S=WASHINGTON, C=US’. This allows anything digitally signed by Microsoft to run. When creating the publisher rule you will be asked to select a reference file, we suggest c:\Windows\Explorer.exe. After selecting the file tick the option to use custom values and enter * for everything except for Publisher.
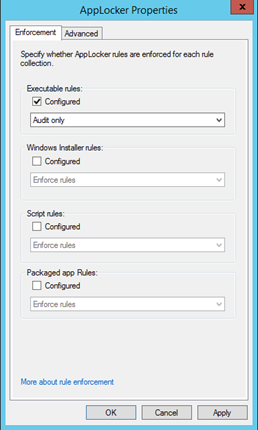
4. Set AppLocker properties for the collections you wish to enforce to be enabled but ‘Audit Only’.
5. Every day for a period of time (we recommend 30 days)
- Capture events logs on the servers were AppLocker is being audited. AppLocker writes Audit logs to the Application event log Microsoft-Windows-AppLocker. Where an item would be blocked by policy a warning event is written.
- Review the captured events and amend the AppLocker policy and add a suitable rule to allow any items that would be incorrectly blocked. We recommend using a publisher rule where possible and avoiding the use of wide-ranging wildcards such as C:\\Program Files\\*6. Agree with any service management you have on an expedited way for users to report items that are incorrectly blocked once the policy is changed to enforce the rules. This is important to ensure that if anything is missed users are not impacted too much.
7. By the end of the 30 days the number of audit warnings should be very low since you will have added rules to allow the items needed for your environment. You can now amend the AppLocker Policy and set the collection ‘Enforce Rules’ rather than ‘Audit Only’.
It might seem obvious but when adding rules to AppLocker it is important to remember why you are doing it and avoid adding rules that could allow something unintended to run. If you add the default AppLocker rules then one of them allows file path C:\Program Files\*, this means any executable within this location can run, including any malware that has been able to write itself to this location. Our advice is to add rules for required software separately to provide more protection for your environment.
The biggest part of configuring AppLocker is the daily task to add the required rules in for your environment. To help capture the rules we used our own debugging tool Lumberjack Pro to capture the AppLocker event logs from all applicable servers every day on a schedule. We then used the grouping options within the tool to group events that were same together to help make the list more manageable. This template can be imported into Lumberjack Pro to direct it to the correct event logs to capture.
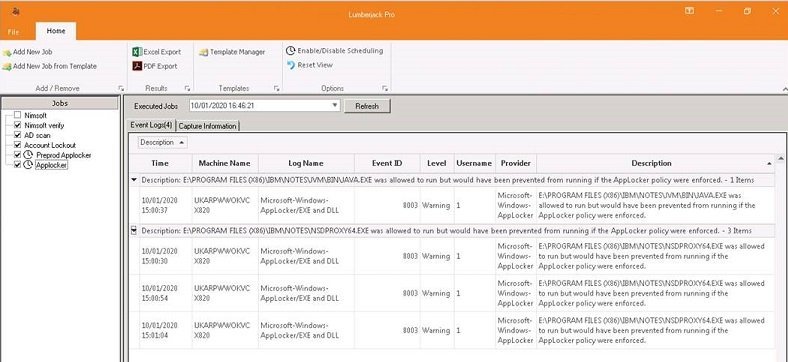
In summary, AppLocker is an excellent and underused feature of Windows. Through proper planning and configuration it can be used to greatly reduce the chances of malware and ransomware from running within your environment. Most companies react to a malware or ransomware outbreak when it happens and finally put appropriate.

